What is API hashing and how it enables red team trade-craft?
Learn what is API hashing and how to use it for red team trade-craft.
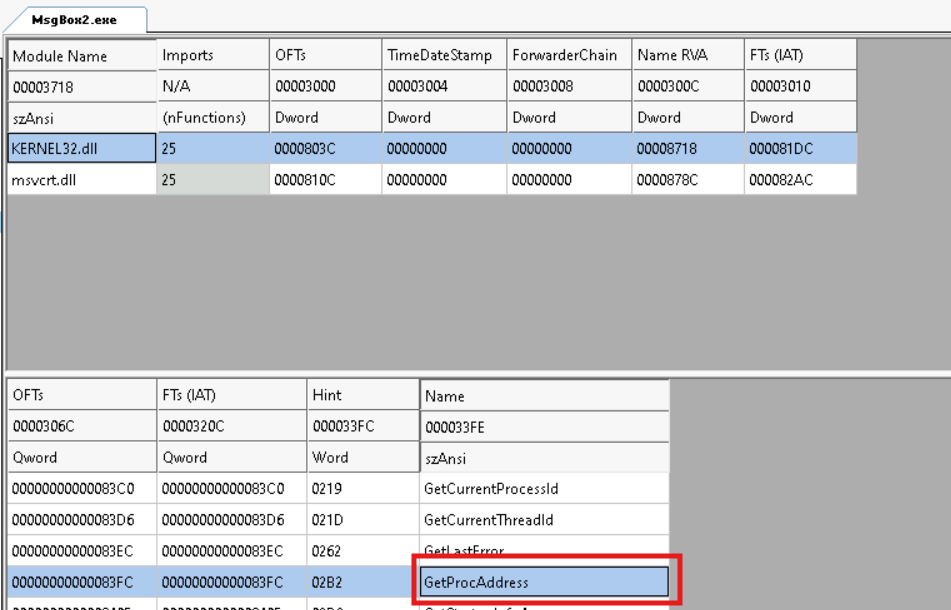
Typically, whenever a piece of code needs to call a Windows API, it references the same by its name. This results in the API name being part of the code as well as the Import Address Table (IAT) of the executable. For a non-malicious application, this isn’t a problem. However, for a malware or a red team operator crafted payload this poses a big problem. For example, an endpoint detection solution can figure out if the payload is up to something mischievous by analyzing the APIs it is referencing.
One way to avoid this is by using the GetProcAddress() Windows API to resolve the required Windows API during runtime (i.e. dynamically). This solves the problem to a certain extent. The name of Windows APIs referenced in the payload will not be part of the IAT. However, GetProcAddress() API will appear in both, code and the IAT. A malware analyst can reverse engineer the malware and figure out which Windows APIs are being resolved by the GetProcAddress() API.
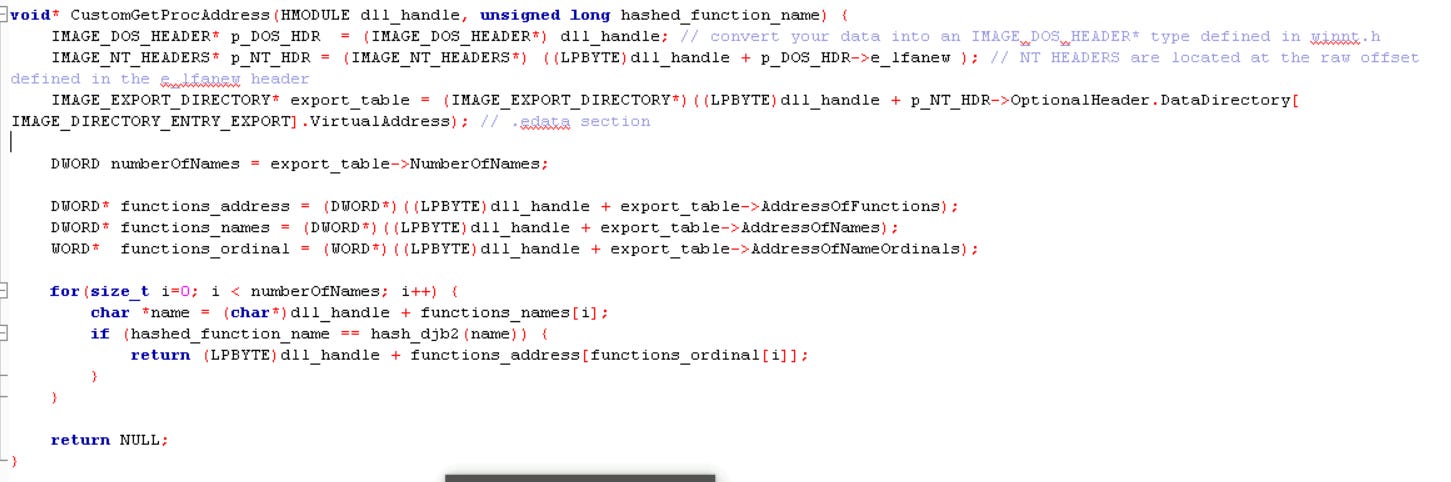
So, we need to figure out a way that can obfuscate the usage of GetProcAddress() API itself. This can be done through a technique known as API Hashing.
In API Hashing, unique hashes are created for Windows APIs and these hashes are then used to search for the required Windows APIs from the respective library. This requires a custom method / function which can dynamically resolve the address of a Windows API through a given hash instead of its name. This means we’ll need to create an alternate implementation of the GetProcAddress() API.
Red Team Notes
- API Hashing is technique in which unique hashes are created for Windows APIs and these hashes are then used to search for the required Windows APIs from the respective library instead of their names.
- It is a type of API Obfuscation technique.Follow my journey of 100 Days of Red Team on WhatsApp or Discord.
The code shown in above snippets is available in 100 Days of Red Team GitHub repository.
Below is a short demonstration of API Hashing in action in my lab.
Examples of real-world malware / cyber-attacks where this technique was used include Lazarus Group, Pteranodon and Latrodectus.
Here’s a video from OALabs that shows how to reverse engineer API hashes:
References
Hackers No Hashing: Randomizing API Hashes to Evade Cobalt Strike Shellcode Detection (must read)
API-Hashing in the Sodinokibi/REvil Ransomware – Why and How?